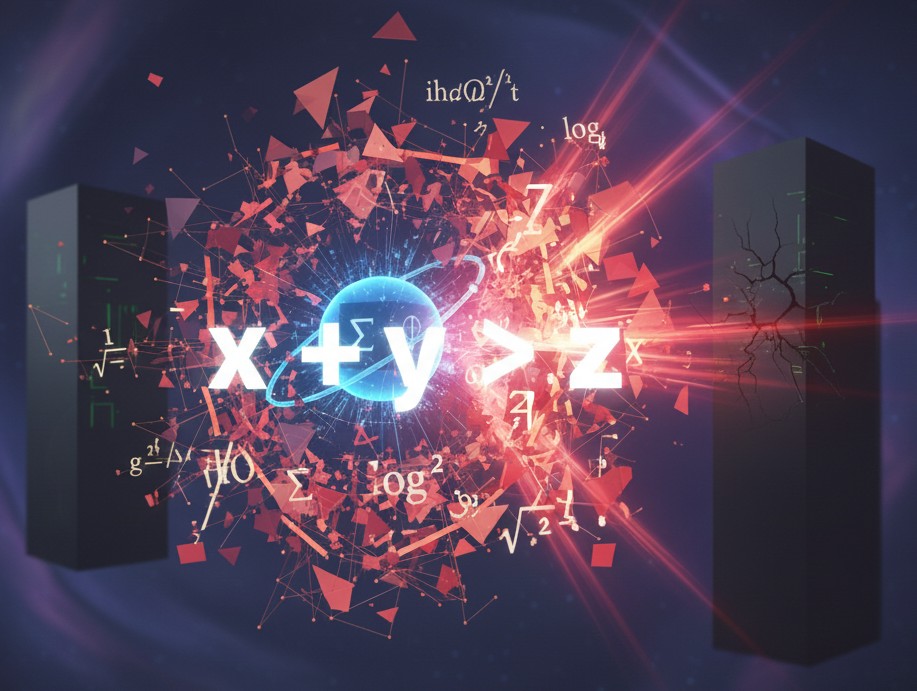
Introduction
Modern digital infrastructures rely on cryptography as a foundational control for confidentiality, integrity, authentication, and non repudiation. These guarantees are not abstract properties but operational assumptions embedded into protocols, hardware, software supply chains, and institutional processes. They enable secure communication, trusted software execution, identity binding, and the long term validity of records.
Quantum computing represents a structural challenge to this foundation. It introduces a computational model capable of efficiently solving specific mathematical problems that underpin widely deployed public key cryptosystems. While large scale fault tolerant quantum computers do not yet exist, the cryptographic threat they pose is not hypothetical in the temporal sense. Decisions made today about encryption, signing, and key management determine the security properties of data and artifacts that may need to remain trustworthy for decades.
This creates a mismatch between the lifecycle of cryptographic assumptions and the lifecycle of information, infrastructure, and institutions. The resulting risk is not adequately captured by asking when quantum computers will arrive. It must instead be reasoned as a time bound inequality involving data longevity, system migration inertia, and cryptanalytic feasibility.
Michele Mosca’s formulation of this problem as a simple inequality provides a precise framework to reason about quantum risk without relying on speculative forecasts1. It translates quantum computing from a future technology concern into a present governance and architectural problem, directly relevant to enterprises and public institutions today.
1 See: Mosca M. Cybersecurity in an Era with Quantum Computers: Will We Be Ready? (2018). IEEE Security & Privacy, vol. 16, no. 5, pp. 38-41, September/October 2018. DOI. Abstract: Organizations must understand their specific risks and plan for their systems to be resilient to quantum attacks. Assessment is based on three quantities: the security shelf life of the information assets, the migration time to systems designed to resist quantum attacks, and the time remaining before quantum computers break the security.
The inequality, explained in plain terms
Mosca introduces three quantities:
- x is the security shelf life. How long the protected information must remain confidential or the authentication guarantees must remain trustworthy. Examples include immediate value traffic with x near zero, versus long lived secrets like health records, trade secrets, defense plans, and long term identity systems where x can be decades.
- y is the migration time. How long it takes to replace quantum vulnerable cryptography across the real system, not the whiteboard system. It includes inventory, dependency mapping, protocol and hardware constraints, standardization, procurement cycles, audits, regression risk, and multi party coordination. Mosca notes y can be very large in ecosystems with many players and constrained environments.
- z is the collapse time. How long until a quantum computer, or any other method, can break the currently deployed public key cryptography at relevant scales.
The risk condition is:
If x plus y is greater than z, then you have a serious problem today.
Reasoning from first principles:
- At time now, you still use quantum vulnerable public key crypto in systems that will remain in production during the next y years, because y is how long migration takes.
- Any data, signatures, or encrypted assets produced and stored during that y year window inherits a required validity horizon of x years into the future, because x is how long it must remain safe or trustworthy.
- If the collapse time z arrives before that combined horizon expires, then an attacker who obtains the protected material can break it within the window where it still matters.
This yields the intuition often summarized as harvest now, decrypt later, but the inequality is broader than confidentiality. It also applies to authenticity and integrity if you store signed artifacts that must remain verifiable as genuine for many years, such as signed software, signed firmware, signed documents, long lived certificates, and compliance archives.
Mosca’s framing is useful because it converts an argument about forecasting into a governance inequality: you can reduce x, reduce y, or increase effective z by retiring vulnerable surfaces earlier, but you cannot negotiate with the algebra once z arrives.
What the inequality means for enterprises and institutions
The central implication is governance, not math
Most organizations instinctively focus on z, because it feels like a technology forecast question. Mosca explicitly shifts attention to x and y because those are under organizational control.
An enterprise cannot control when large fault tolerant quantum computers exist. It can control:
- Which assets require long term guarantees, meaning x by asset class.
- How quickly it can migrate cryptography across business processes and technical estates, meaning y.
This immediately reframes quantum readiness as an internal capability question: cryptographic agility is a business capability with measurable lead time.
x is a policy decision, and many firms underestimate it
In practice, enterprises often treat x as retention period or compliance archive duration and forget that business value can outlive retention rules.
Examples where x is long even in commercial settings:
- Trade secrets embedded in engineering drawings, process recipes, firmware, and source code.
- Identity binding artifacts, such as signed statements, audit trails, notarized documents, and long lived device identities.
- Safety and liability records where future disputes depend on authenticity of archived material.
If these remain valuable for decades, then x is decades, regardless of whether the system generating them feels operationally short lived. Institutions often have even longer x: national archives, census data, public registries, land and property records, court evidence, and critical infrastructure telemetry.
y is usually the dominant risk driver
Mosca highlights that y can be small in a centrally controlled product that can auto update a symmetric key size, but can be fifteen years or more when it involves public key standards, constrained devices, and multi party agreement.
From an enterprise architecture viewpoint, y is large when any of the following are true:
- Embedded devices with long replacement cycles exist, typical in OT, medical devices, industrial sensors, automotive, and aerospace.
- There are external interoperability boundaries, such as suppliers, customers, banks, clearing houses, government interfaces, and cross border protocols.
- Cryptography is implicit in vendor products where you cannot upgrade algorithms without platform refresh.
- There is no inventory of cryptographic dependencies, meaning you cannot even scope the migration.
In other words, y is large when cryptography is not managed as a lifecycle component of architecture.
Practical consequence: quantum risk is already a data risk and a signing risk
Even if you believe z is far away, the inequality says the present day decision is about what you are producing and storing now that must remain protected for x years, while you still have y years of migration ahead.
Two concrete enterprise risk categories follow directly.
- Confidentiality risk. Anything encrypted today with quantum vulnerable public key mechanisms used to establish session keys, distribute keys, or wrap data keys can become readable later if recorded now.
- Authenticity risk. Anything you sign today with RSA or ECC and expect to remain a durable proof of origin may become forgeable later. That impacts software supply chains, device firmware provenance, contract authenticity, and long lived certificate ecosystems.
This is why we will fix it when quantum arrives is logically inconsistent if x plus y is greater than z. The artifacts you create during the wait are the exposure.
The solution landscape in Mosca’s framing
Mosca separates two complementary solution families:
- Post quantum cryptography. Conventional algorithms believed to resist known quantum attacks, usable on conventional hardware, still based on computational hardness assumptions. Quantum cryptography, especially QKD. Uses quantum channels for key establishment and aims to avoid computational assumptions for that function, at the cost of requiring quantum communication infrastructure and operational constraints.
Mosca’s key architectural point is that the ecosystem is strongest when both exist, because they occupy different cost, assurance, and deployability points. He also notes combinations can provide properties hard to obtain with only conventional public key cryptography, for example pairing QKD based key establishment with post quantum signatures.
For enterprises, the actionable takeaway is not choose one. It is design migration pathways that can incorporate both, depending on asset criticality and channel feasibility.
Enterprise and institutional actions derived from the inequality
Everything below is derived from controlling x and y:
- Classify assets by required security horizon x. Do not start with algorithms. Start with asset classes and decision rights. Define x bands such as real time, one year, five years, twenty years, and indefinite.
- Build a cryptographic bill of materials. Inventory where public key crypto appears: TLS termination, VPN, email, document signing, code signing, device identity, HSM usage, PKI, SSO tokens, backups, and archival systems. If you cannot enumerate it, you cannot reduce y.
- Prioritize surfaces that create long lived artifacts. Code signing, firmware signing, and long retention document signing usually dominate authenticity exposure. Key wrapping and archival encryption dominate confidentiality exposure.
- Demand cryptographic agility from vendors. Procurement language should require algorithm agility, upgradeability, and roadmaps aligned to PQC standards trajectories. This reduces y structurally.
- Pilot post quantum transitions where blast radius is controllable. Begin with internal services, controlled endpoints, and gateway termination where you can swap algorithms with fewer external dependencies.
- For high assurance channels, evaluate quantum key distribution only where operationally justified. QKD is not a blanket internet solution today, but it can be meaningful for specific point to point links with extreme requirements and clear cost justification, as Mosca notes.
- Institutional governance: mandate a plan, not a prediction. Mosca’s note explicitly emphasizes that business and policy decisions drive adoption, and that asking organizations to articulate a plan is a powerful lever.
If you want a single sentence governance test derived from the paper, it is this: for every critical asset class, document x, estimate y from your architecture realities, and then decide whether you can tolerate the residual risk that z may arrive before you finish.
Closing interpretation
Mosca’s inequality is valuable because it forces temporal reasoning. The debate about when quantum computers will break RSA can remain uncertain. The inequality still compels action because x and y are often large, and both are created by present day organizational choices.
Enterprises and institutions that treat cryptography as a static technical control will discover y is longer than they assumed. Those that treat it as an architectural lifecycle capability can compress y, narrow the set of long lived quantum vulnerable artifacts they produce, and therefore reduce exposure even under uncertain z. That is the practical meaning of the inequality.